Cyber Security
- Home
- Cyber Security
Protecting You From Cyber Threats
We offers professional cybersecurity services for small to medium sized businesses and to larger enterprises looking to expand their cybersecurity capabilities. Our experts, utilizing an in-depth understanding of the attack landscape from the perspective of an attacker, take a hands-on approach to provide end-to-end cybersecurity solutions that are both effective and practical for each organization’s unique needs.
Our Approach
We brings a unique advantage to our customers. By working with our clients to identify specific cybersecurity gaps within their organization, We provides tailor-made services and domain expertise to create a proactive cybersecurity defense to address those gaps. As an extension of the customer’s team, We provides cost-effective and highly-skilled services to augment the organization’s security capabilities.

Our Solutions

Risk Management
Risk management program is tailored to meet the needs of each specific client. it serves as a roadmap to help understand organizational liability and mitigate risks. the resulting plans account for the client’s available budget, approach to governance and risk tolerance, 3rd party risks, and the maturity of policies and procedures.
Security Survey
Risk-based approach aims at risk reduction as the primary goal. This enables the organization to prioritize investment and focus on building appropriate controls for the most damaging threats to the business’s most critical assets.
Penetration Testing
We work to develop a risk management program catered to our clients and serve as roadmaps to help understand organizational liability and mitigate risks. These plans consider the client’s approach to governance, risk tolerance, the maturity of policies and procedures, and 3rd party risks managed within the available budget

Application Security
Integrate Security into Your Product DNA
Our application security teams can help in every stage of the application’s lifecycle, from design/architecture to deployment. Our experts have deep experience developing and coding in broad types of applications and domain environments, including Web, Cloud, Mobile, IoT, Embedded, etc.
We works closely with customers to educate their employees in developing secure applications. We assess the systems to identify and mitigate vulnerabilities, and help build safeguards to keep our clients' application security one step ahead of the hackers.

CISO as a Service
Cybersecurity threats present significant risks to small and medium businesses, particularly those using software-as-a-service (SaaS) providers. However, attracting and retaining the right leadership to address this challenge is not financially feasible for many organizations. The shortage of talent in Information Security, along with the level of effort needed (not a full-time job), contributes to the challenge of employing a full-time CISO. The Our Advisory CISO service is designed to assist small-to-medium business develop a right-sized security program to allow for organizational growth over time.
Cloud Security
Organizations moving more and more information into cloud services, the classic concept of perimeter-based security has become outdated. companies must adopt new governance methodologies and undergo a paradigm shift in their information security logic. This often requires getting assistance from third-party providers that have the skills needed to overcome cloud security challenges.
Cloud security is a shared responsibility between the provider and the consumer. However, the accountability of the data will ultimately fall on you as the provider. Our cloud security team will help you determine your specific security responsibilities within your unique cloud implementation, and how you can best govern those responsibilities. This includes helping you identify and acquire the necessary skill sets, tools, and build methodology for auditing and monitoring your organization’s information.

Threat Intelligence
Cyber threat intelligence is information about cybersecurity threats and bad actors.
this information is very important to help mitigate attacks against your networks and information systems. threat intelligence sources include open-source intelligence, social media intelligence, human intelligence, technical intelligence, or intelligence from the clear & dark web.
Our service provides vital information which enables you to proactively defend against existing and future Cyber events. It gives a broad, intelligent picture regarding attackers that may be, or ever are targeting your organization, and how your information systems are being viewed from outside your network. It also shows how your particular business sector and geography are impacted, and even your particular brand.
Our team is on the hunt, with 24/7 capabilities of collecting, analyzing, and reporting any type of digital information. Combining cutting-edge technology (as well as OSINT capabilities) and top-level expertise, our team of Cyber Experts and Intelligence Analysts gather information from multiple resources (Darknet and Deep clear web included), in order to deliver a comprehensive, up to date and relevant and view of the cyber threats landscape. This information is essential for planning and updating the organizations control for defense.

SOC as a Service
Access to around-the-clock expert cybersecurity coverage is within reach with our soc-as-a-service. free your resources and dramatically improve your security posture — without losing visibility into your environment.
SOC as a Service Include the following services:
A well aligned and optimized Monitoring plan that clearly identifies your business risks and desired business outcomes, and then continuously monitors your system and threats against these established goals and objectives.
A fully managed, purposefully developed SOC, SIEM and Log Management
Service24/7support, including:

Cyber Liability
In under 3 minutes, get an instant cyber liability quote that includes risk reduction management and employee training, at no additional cost.
CYBERSECURITY IS NOT JUST A SERVICE; IT'S AN INVESTMENT IN SAFEGUARDING YOUR DIGITAL FUTURE.
What separates us from the Competition?
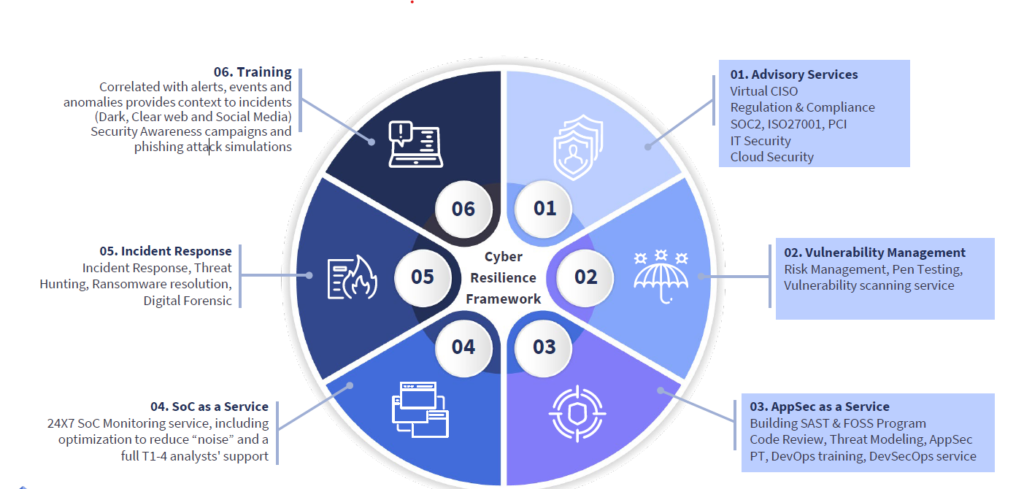
Cyber Resilience Management Services
Contact Us
Please leave your contact information and we will contact you to shortly.